In January 2021, Florida Healthy Kids Corporation reported one of the biggest healthcare data-security breaches, globally, to date. A startling 3.5 million individuals were impacted by the breach, giving cyber-criminals access to crucial data, such as social security numbers, birth dates, names, addresses, and financial information. The vulnerabilities that led to this cyber-attack were present in the organization’s system since 2013. This, however, is far from an isolated incident, and data suggests that the number of attacks on the healthcare industry is only set to increase, moving forward.
To counter this, healthcare stakeholders in various countries are collaborating to address cybercrime threats, identify vulnerabilities in operating systems, and coordinate responses to minimize the impact. We spoke to Saurabh Gupta, Innovation Research and Business Strategy Expert, about the scope of digital health cybersecurity and the importance of robust backend infrastructure to prevent future cyberattacks.
1. With the pandemic pushing digital health into the spotlight, how much importance do cybersecurity and data privacy hold in this context?
Digital health (specifically telehealth) has been at the helm of delivering quality care services during COVID-19 pandemic times. Considering that, the present scenario is all about streamlining the operational capabilities and further penetrating its adoption amongst the various stakeholders, including policymakers, patients, caregivers, insurers, and the system providers.
The healthcare industry (often termed as ‘compliance industry’ because of stringent rules and regulations) has been the sweet target spot for cybercriminals even in the past, allowing them to attack the vulnerabilities of the patients and healthcare providers (HCPs). This is primarily due to the breadth of the organizational network, starting from hospitals to pharmaceutical companies and diagnostic facilities, and now extending to the patient’s homes wherein the data is generated in the digital health era.
Many patients and consumers are already adapting to using sensing devices that monitor their vitals and activities. The convergence of all the information present from these devices will raise the following concerns, for which they will seek transparency, clarity, and assurance:
- Who will record and store their health information?
- Who all are monitoring their information?
- Who all have the authorization to access that information?
- What is the information used for?
- How is the sanctity of the information maintained?
- How and to what extent, is their information secure with the data storage and management nodes in the network?
- What will be the possible repercussions and measures, in case of their privacy breach?
2. How has the digital health boom exacerbated the issue of cyberattacks?
We all would have heard of the famous WannaCry ransomware attack on the UK’s National Health Service (NHS) in 2017, which impacted over 80,000 hospitals and care centers across the country. And this attack was not even meant for the healthcare industry!
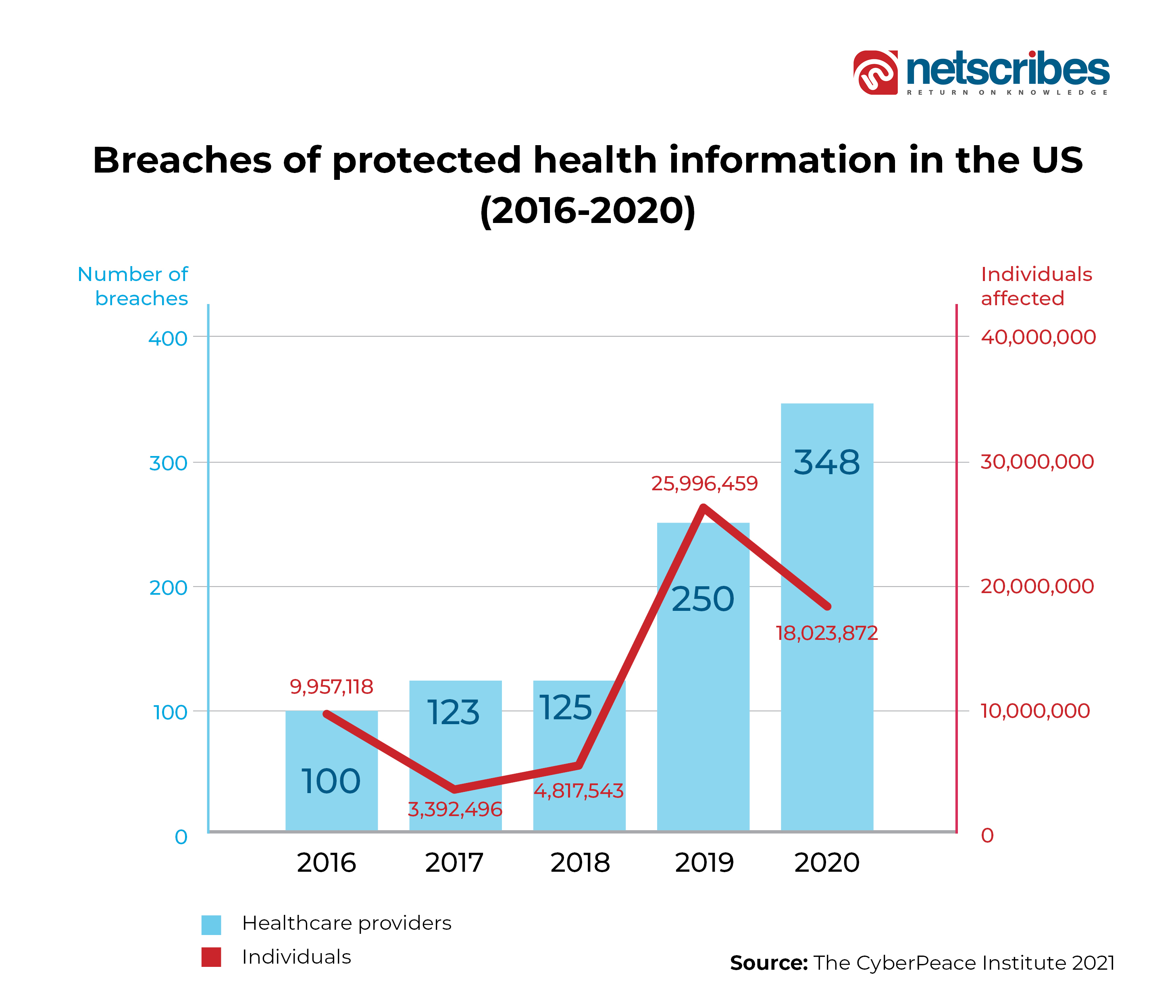
Even 2021 witnessed over 1,100 attacks on the healthcare records in more than 30 countries, which resulted in a cumulative breach of a staggering 120 Mn+ records (average of around 150,000 records) containing sensitive information such as medical records, financial, and social details.
“Dark web pays up to 10x–15x more for the breached health records than the financial details. And the startling fact doesn’t end there: to add on top of it, the healthcare companies pay almost 4x–5x more to retrieve the stolen health record, compared to the companies in the other industries.”
The above figures make it very clear that these healthcare organizations are an enticing target for cyber attackers. Since the health systems link thousands of locations operating on a mix of wired and wireless networks, it becomes very easy for the attackers to move between the geographical locations, after successful infiltration of the hospital/healthcare network with something as simple as phishing.
Further, now with the rapid digitization of the patient records (EHRs) and collecting patients’ health information using IoMT and connected devices, the ground surface for the attacks has exploded in all senses. This global network of devices, currently standing at ~10 Bn, is expected to grow at a CAGR of 19.6% to around 50 Bn by 2030.
Why is this so, is also interesting to understand. Now, the attackers will not need to only focus on ransomware, information misalignment, or cyber espionage as the potential attack modes. Rather, they will be able to hold hostage all the connected medical devices through a simple ‘Denial-of-Service (DoS)’ attack, while also encrypting the critical data and accordingly, bringing the entire network down.
3. In this light, what are the recent regulations that have come into play for digital health cybersecurity and data privacy?
In the US, the Department of Health & Human Services (HHS) in sync with Section II of the Health Insurance Portability and Accountability Act (HIPAA) and subsection D of the Health Information Technology for Economic and Clinical Health (HITECH) Act has laid the security and privacy safeguard standards for ‘Protected Health Information (PHI)’. This PHI is the crucial health information identified for a patient including physical and mental health, provision, and payment for healthcare services. HHS has issued three broad sets of regulations namely, Privacy Rule, Breach Notification Rule, and Security Rule.
The Food and Drug Administration (FDA) is responsible for regulating the privacy and cybersecurity matters related to medical device manufacturers, providers of Software as a Medical Device (SaMDs), and EHR providers, involved in the digital healthcare ecosystem. There is also the Federal Trade Commission (FTC) which addresses the unfair and deceptive trade practices legally, under the Federal Trade Commission Act.
Australian Digital Health Agency works closely with the country’s Cyber Security Centre (CSC) to ensure the protection of digital health assets.
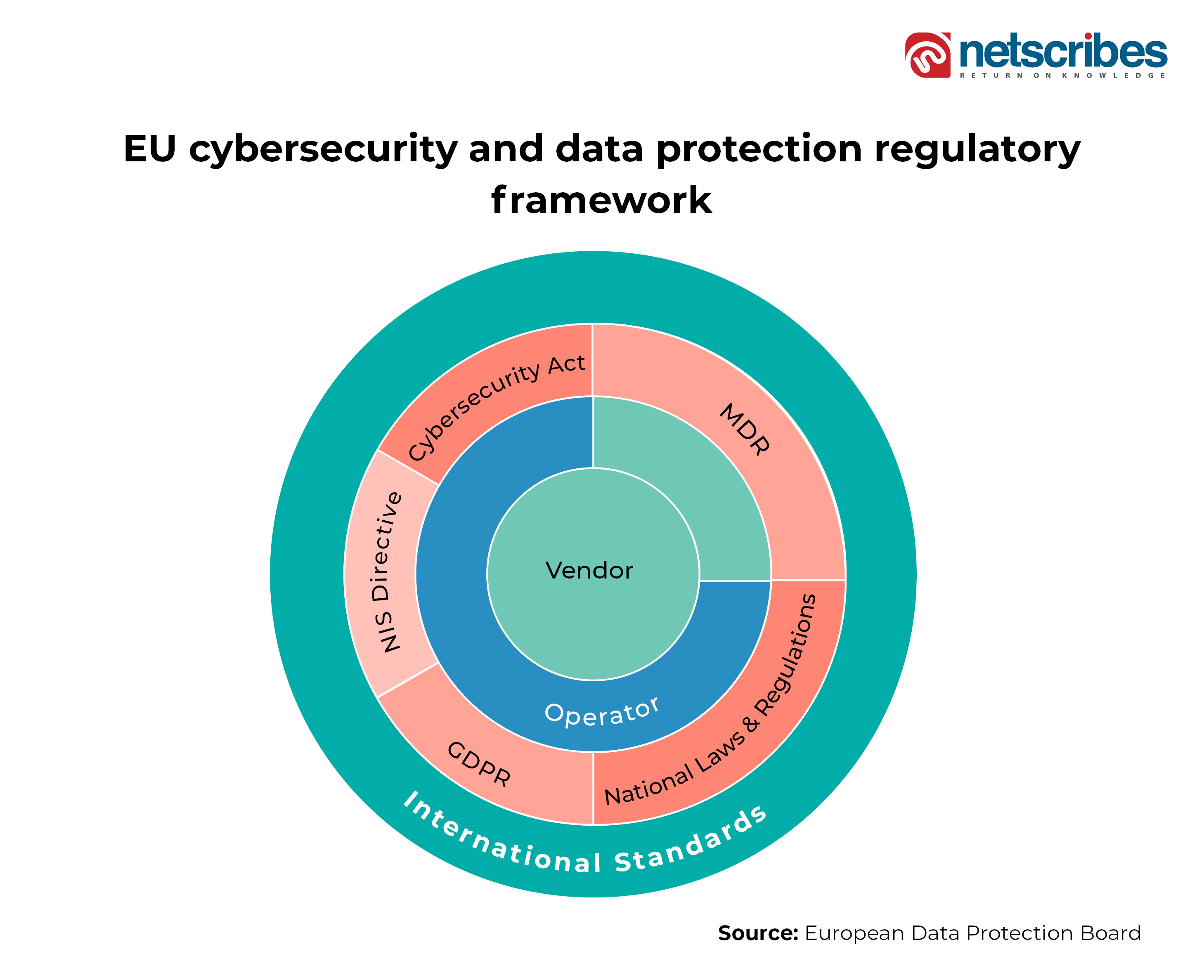
On the other hand, the EU region is monitored by the COCIR (region’s healthcare coordination committee), which has introduced cybersecurity requirements for devices, infrastructure, equipment, and systems. While Medical Device Regulation (MDR) introduces devices’ security, Directive on Security of Network and Information Systems (NIS) provides legal measures for overall cybersecurity in the region. The General Data Protection Regulation (GDPR) introduced stringent rules on the processing of individuals’ data records, and the Cybersecurity Act provides for European cybersecurity certification at individual countries’ levels. The below figure provides an overview of the European cybersecurity and data privacy mechanisms for digital healthcare.
Traversing further east, there is the Cyberspace Administration of China (CAC), which is responsible for setting the healthcare data privacy and protection standards. There is also the National Health Commission (NHC) to maintain the national health data. The Cybersecurity Law 2017 acts as the ground for data regulation including digital health data records. Even the healthcare apps are governed under the medical device and general applications regulations.
4. What are some of the major digital health cybersecurity frameworks that are being implemented across the globe? Can you please give us some examples?
Putting it upfront, cyberattacks and cybersecurity threats are not getting eliminated. So, device manufacturers, hospitals, and facilities must work to manage them. Compliance is important, but securing data is not just checking off the compliance tick-boxes.
Realizing this, a lot of companies have now made cybersecurity and data privacy an enterprise-level strategy vertical. There are designated people at the CIO or CISO levels, responsible to lead the IT-security programs, with sufficient authority and efficiency. These designated personnel have developed business risk mechanisms to assess the impact of security risks on business operations.
There is an increased emphasis on data encryption, anonymous storage of PHI, and reduction in data sharing outside the healthcare network. Further, recurring usage of stronger passwords is being enforced alongside 2-factor authentication schemes to secure the devices on the companies’ networks.
Companies are also focusing on conducting due diligence of the third-party vendors before sharing access to PHI, by regularly auditing their vendors’ SOPs for encryption, firewalls, admin management, data management, password change policies, etc. They are also putting into place stringent NDA guidelines with penalty clauses, in case of any incident of mishandling of the critical data.
Even policymakers while regulating digital health products have framed a recommended 6-steps approach to protect the data from cyberattacks:
- Build security awareness among the company, its employees, vendors, suppliers, and distributors
- Keep the software applications updated
- Use strong passwords, implement multi-factor authentication, and change passwords regularly
- Regular back-up of the data
- No response to phishing emails, texts, and calls
- Upon becoming a victim of ransomware/cyberattack, avoid paying the ransom. Rather, report the incident to the security authorities of the country/region.
5. How does the regulatory landscape for digital health cybersecurity differ across developed nations (for instance, the UK and the US), as compared to developing nations (for instance, APAC)? Can you please illustrate with an example?
There are a lot of laws, rules, regulations, directives, and guidelines directly or indirectly governing the cybersecurity requirements for the healthcare industry. Understanding the implications of these regulations has become crucial for any entrant into the digital health industry. Even though these laws are a good starting point, they themselves aren’t sufficient to mitigate the future cyber risks on their systems. Each country has its cybersecurity and data protection/data privacy regulations, which encompass all industries generally, including digital health.
Countries that are early adopters of digital health such as the US, EU, China, Singapore, and Israel have established and enforced separate regulations specifically focusing on medical devices, SaMDs, apps, and other health collecting sensing devices which become part of the healthcare network. Compared to this, the laggard adopting countries are envisaging data privacy, protection, and cybersecurity guidelines in general, encompassing the healthcare industry as well. With the boom in digital health in these countries, the scenario is expected to change, with intensive focus drawing towards the sensitivity of the health data records in these countries as well.
6. What is the role of inter-organizational cooperation in strengthening cybersecurity initiatives?
There is a need to balance protecting patient safety and promoting the development of innovative technologies and improved device performance. The healthcare organizations will have to expand their focus on securing, not only the legacy systems currently but also the connected devices integrating into their networks at an unprecedented pace. These connected devices (specifically class 3 medical devices) don’t have standardized security measures in place. With their deployment across the healthcare network, new risks and vulnerabilities have been introduced, which can potentially impact the patients’ lives.
There will be a new vigor among the CIOs, CTOs, and security leaders, to develop and implement new compliance policies for protecting these additional devices on the hospital network. Their focus will be on re-evaluating their IT security (IT-Sec) infrastructure, potential attack exposure gaps, and ways to strengthen their data security governance mechanisms. There will also be stronger linkage and integrated responsibility-sharing between the biomedical and the IT-Sec teams, to take higher control over security measures implemented over such connected medical devices in the hospital’s ecosystem.
7. How can the digital health security infrastructure be improved from the back-end?
There should be a ‘secure-by-design’ principle inherent in the development of new software and security systems, meaning placing security at the core of the product development rather than adding it on top, to just envelope the core security loopholes.
Healthcare companies should strategize their focus on ensuring the security and sanctity of the PHI available to them. This will, to a large extent, mean increasing their cybersecurity budget, to not only secure the infrastructure, update systems, and equipment, and patch the identified vulnerabilities, but also embed a cyber secure-aware environment within the company and its employees. They should also be transparent in committing to the due diligence of their IT infrastructure and reporting cyber incidents.
8. What strategy will be executed to implement a robust cyber-secure digital health ecosystem?
2020 onwards had brought in a paradigm shift towards the way healthcare was delivered, by exponential adoption of digital health mechanisms such as mHealth, Telehealth, and remote care. This has generated enormous amounts of data across the endless nodes, allowing healthcare industry CXOs to move towards organizational, data-driven decision-making.
2022 and onwards will see the CIOs focusing on establishing a “data strategy” that will be governed and planned to encompass disparate data sources such as apps, the Internet of Things, wearables, sensors, and edge devices. Governance will become mission-critical from a healthcare delivery perspective, as healthcare systems will have to standardize the different types, quality, and frameworks of data generated and transmitted by different devices.
This data strategy will further entail an infrastructure boost to shift towards storage, manage, and using the data effectively. Hence, companies will see shifts from just cloud to data warehouses, data lakes, and the upcoming “data lake house”, which will provide enhanced capabilities to save, administer, and orchestrate the data.
These new capabilities include the data mesh, which comprises loosely coupled services architecture to allow organizations to integrate and share data at scale.
Healthcare data in the digital health era will require greater emphasis on data operations as organizations must curate and manage data as an asset and create a reusable data product. To prepare for this shift now, healthcare leaders must evaluate their data operations capabilities and ask themselves three key questions:
- What is our data tech strategy to make this transition?
- What does our data mesh look like?
- What people and processes do we need in place?
9. Going forward, how can digital health stakeholders balance interoperability with data security?
The CIOs and CISOs will have to first understand the requirements and restrictions of all, data security, data privacy, and interoperability rules, correctly, to strike the right balance. An interoperable ecosystem will enable seamless and secure data exchange by and between the stakeholders.
To ensure seamless adoption of digital health, there will be a need for a national and global blueprint, which allows open-source health data standards including reusable interoperable assets. This will establish a novel integration of various digital technologies, while also ensuring good quality standardized data. For the same, there will be a need to also set up robust health IT infrastructure, which will depend on generally identified conditions in the public health segments, defined standards, and technical and functional specifications. Based on strict regulatory norms, the systems will guarantee PHI’s data protection, privacy, and sanity.
All this, easier said than done, will further entail all the participating stakeholders (patients, HCPs, caregivers, payers, and insurers) to undergo a reliable identification, verification, and authorization protocol digitally, for trust mechanism implementations, before obtaining access to the PHIs.

Saurabh Gupta
Innovation Research and Business Strategy Expert
Saurabh has been working in the strategy consulting and advisory role for over nine years, closely working with global clients on resolving their complex business and operational challenges across the sales, marketing, IP legal, and ops functions. When it comes to the healthcare industry, he has specific interests in the med-tech, digital health, and transformational technologies sectors. In his free time, he loves traveling, hiking, reading, and spending quality time with family.




